CVEs: an introduction

CVE stands for Common Vulnerabilities and Exposures, and it's a database of publicly documented data security flaws. The CVE number is a unique identifier for one of the vulnerabilities in the list. CVE provides a simple and secure means for suppliers, businesses, researchers, and other interested parties to share information regarding cybersecurity threats. CVE and its accompanying CVSS scores are commonly used by businesses for vulnerability management planning and prioritizing.
CVE was created in 1999 and is handled and maintained by the MITRE Corporation's National Cybersecurity FFRDC (Federally Funded Research and Development Center). The US Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA) both contribute operating funds to CVE, which is funded by the US Federal Government. CVE is a public database that anyone can access and use for free.
Vulnerabilities and Exposures
A vulnerability is a flaw in a computer system that can be exploited to obtain unauthorized access to it or execute unauthorized actions on it. Attackers can use vulnerabilities to get direct access to a system or a network, run code, install malware, and gain access to internal systems in order to steal, delete, or change sensitive data. It could allow an attacker to impersonate a super-user or system administrator with complete access privileges if it remains undiscovered.
An exposure occurs when a user makes a mistake that allows an attacker to gain access to a system or network. Attackers may be able to obtain and exfiltrate personally identifiable information (PII) as a result of security flaws. Accidental exposure, rather than sophisticated cyber attacks, was the cause of some of the largest data breaches.
Why use CVEs
All companies benefit from sharing CVE information since it lets them to establish a baseline for evaluating the coverage of their security tools. CVE numbers assist enterprises to see what each tool covers and whether it is acceptable for their needs. Organizations can quickly and accurately access information about a particular vulnerability or exposure by utilizing the CVE ID, and coordinate their efforts to prioritize and remedy these issues to make their organizations more secure. CVE information can be used by security advisories to look for known attack signatures and find specific vulnerability exploits.
Who can report CVEs?
A CVE can be reported to a CNA by anyone. CVE reports are typically found and submitted to one of the CNAs by researchers, white hat hackers, and vendors. Many suppliers actively encourage users to look for vulnerabilities as a "free" way to improve their products' security posture. Many companies even offer bug bounties and other types of contests and incentives to encourage people to test their products' security and uncover holes.
Kepler: Exein opensource CVEs solution
Exein has developed an opensource solution that allows you to always be up to date with regards to CVEs: Kepler.
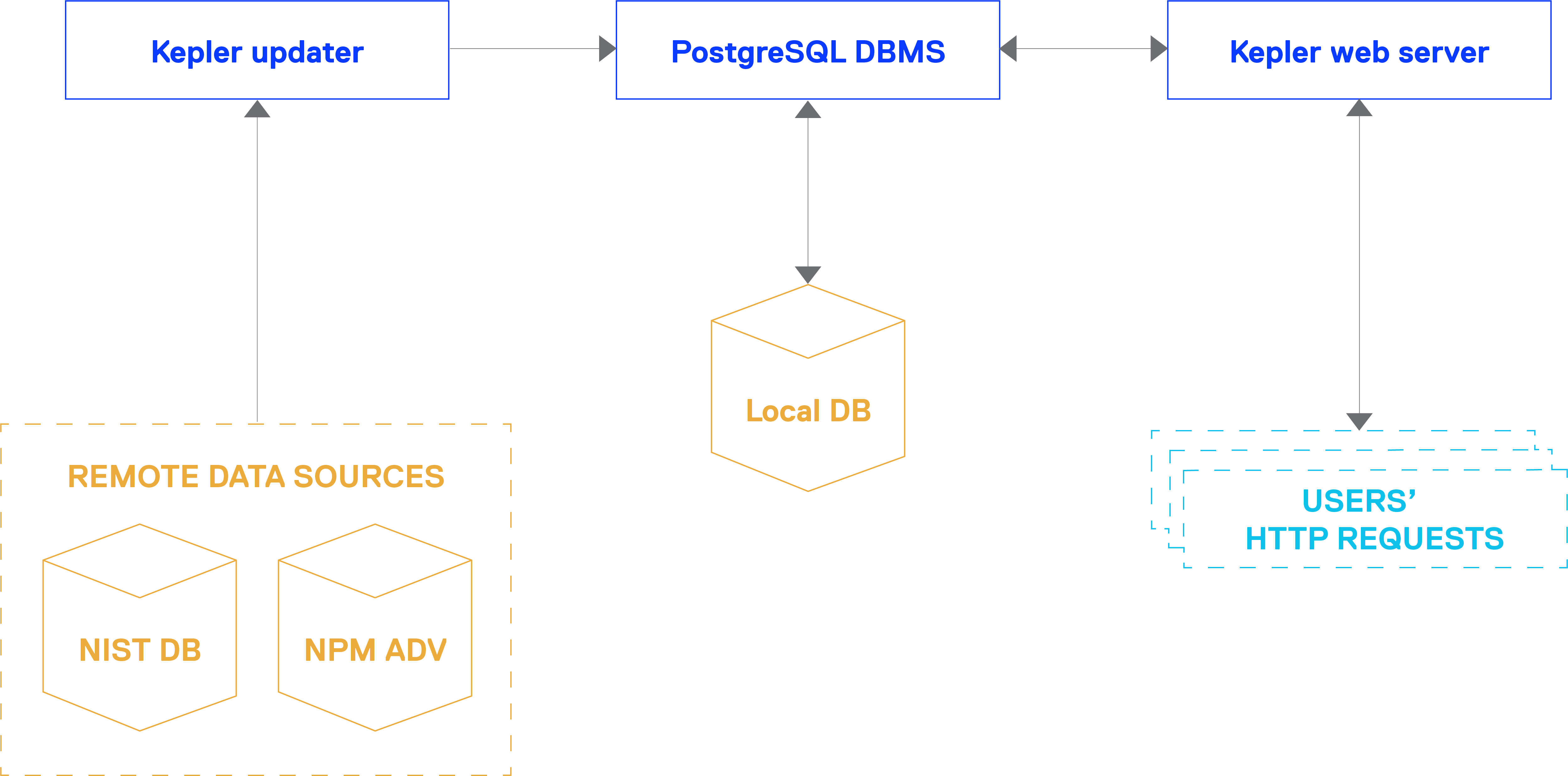
Kepler is a vulnerability database and lookup store which makes use of National Vulnerability Database and NPM Advisories as data sources.
These are the main features of Kepler:
- Multiple CVEs data sources
- Easy-to-use API to search for CVEs by [product, version] couples
- CPE 2.3 tree expressions and version range evaluation in real time
- Periodic automatic synchronization with the data sources
- Self-hosted database for faster searches
- Distributed within a docker image to speed-up the deployment
- Rust-based open-source code available for building
Kepler is based on three main modules that will be available after the build process:
- kepler-postgres, the PostgreSQL database module, which will host the CVEs records downloaded from the data sources
- kepler-updater, a job scheduler used to keep the CVEs database up-to-date
- kepler, the Exein open-source application itself, which manages all the stuff (importing from the data sources and handling the API endpoints)
Take a look to Kepler's GitHub page to learn more and get started!