EU Cyber Resilience Act: Key Points

Navigating new regulations can often be complex, particularly when they impact your development and manufacturing processes. To aid in this, we have distilled the EU Cyber Resilience Act into its key points, providing you with an overview of the forthcoming landscape.
What is the CRA?
The CRA is one of the first legislative proposals of its kind in the world that aims to improve the cybersecurity of products or software with a digital component which are ubiquitous in our daily lives (ranging from baby monitors, smartwatches, and video games to firewalls and routers) as well as to allow consumers to make more informed choices when they select and use IoT devices.
Once the CRA is applied, all products within the scope of this regulation put on the EU market, whether supplied by an EU company or an external one, will have to be secure from a cybersecurity standpoint.
Download The Cyber Resilience Act guide to learn more.
Who is impacted by the CRA?
The Cyber Resilience Act (CRA) is a game-changer for cybersecurity in the EU market, with significant implications for businesses operating within the region. This legislation primarily targets Original Equipment Manufacturers (OEMs) who design and manufacture devices with digital components. The aim is to establish a comprehensive set of requirements, ensuring these devices are built with security at the forefront from the very beginning.
But the impact of the CRA extends beyond EU-based OEMs. Because the Act applies to products sold within the EU market, regardless of the manufacturer's location, OEMs and their partners from other countries will also be affected. This includes authorized representatives, resellers, and distributors. These entities will need to implement processes to verify that the products they handle comply with the CRA's regulations. This collaborative approach across the entire supply chain strengthens the overall security posture of the digital landscape within the EU.
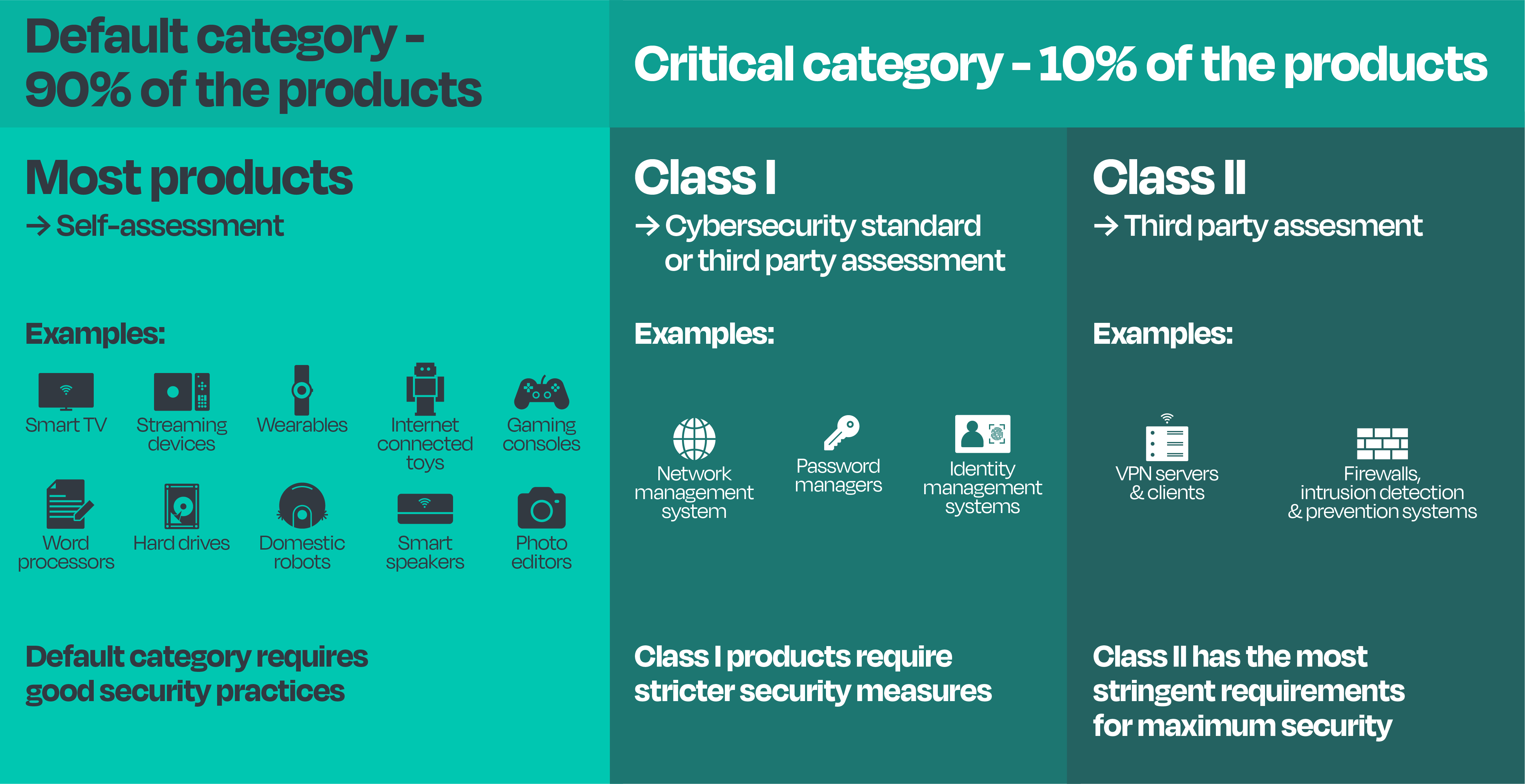
Product Classification under the CRA
The CRA employs a risk-based approach to classify Products with Digital Elements (PDEs) into categories with varying compliance requirements. Here's a breakdown of the classification system:
Default Category (Minimal Risk):
This category encompasses the vast majority of PDEs (around 90%) that pose minimal risk in the event of exploitation. These products typically:
- Don't store sensitive data.
- Don't interact with critical networks.
Examples include: Smart speakers, word processors, photo editors, wearables, internet connected toys, hard drives, smart tvs.
For the default category, manufacturers can achieve compliance through self-assessment and documentation.
Critical Category (Elevated Risk):
Annex III further subdivides the critical category into two classes:
- Class I: These products perform functions (i) crucial to the security of other products, networks, or services. Alternatively, they might (ii) carry a significant risk of adverse effects due to their ability to disrupt, control, or damage other products or endanger individuals.
Examples include: Identity management systems, standalone & embedded browsers, password managers, network management systems, public key infrastructure softwares, operating systems routers, modems, and switches.
Class I compliance requires a standard form (potentially ETSI EN 303 645) or a third-party assessment.
- Class II: This class represents products that meet both criteria defined for Class I (i) and (ii). They pose the highest risk within the critical category and require mandatory third-party conformity assessment for compliance.
Examples include: VPN server and client products, hypervisors and container runtime systems, firewalls and intrusion detection systems.
Legal Obligations Under the CRA
The CRA specifically targets economic operators involved with products that include digital elements (PDEs). This encompasses manufacturers, authorized representatives, importers, and distributors, with a pronounced focus on manufacturers. Here are the key obligations:
- Risk Assessment: Manufacturers are mandated to continuously assess and mitigate risks associated with their PDEs throughout the product's lifecycle.
- Monitoring and Updates: Post-market, manufacturers must vigilantly monitor products for cybersecurity risks and promptly roll out updates, free of charge, for at least five years. If vulnerabilities are detected, immediate action is required.
- Reporting: There is a stringent requirement to report any exploited vulnerabilities and incidents to national authorities via ENISA within 24 hours for early warnings and 72 hours for complete notifications.
- Transparency: Comprehensive technical documentation and user-friendly instructions must be provided, ensuring that end-users are well informed about the security features of the products.
How Exein Supports Compliance with the CRA
Understanding and adhering to these new regulations can be daunting for manufacturers. This is where Exein comes in. Specializing in IoT security solutions, Exein offers a robust suite of tools designed to help manufacturers not only comply with the CRA but also enhance their product security posture:
- Security Posture Assessment: Before IoT devices hit the market, Exein’s assessment tools scrutinize them to ensure they are devoid of vulnerabilities.
- Runtime Threat Detection and Response: Exein’s capabilities extend to real-time, providing dynamic protection against external threats across various platforms, from Docker to RTOS.
- Threat Intelligence: Leveraging the power of generative AI, Exein makes all relevant security information and documentation about devices readily accessible through an intuitive platform.
Why IoT Security Matters More Than Ever
The imperative for stringent IoT security is underscored by the escalating scale and sophistication of IoT threats. IoT protection is not just about securing a single device but safeguarding an entire ecosystem that includes everything from personal smart devices to critical infrastructure components. Secure IoT devices are the cornerstone of not only consumer trust but also the foundational integrity of modern smart infrastructures.
The Cyber Resilience Act (CRA) marks a significant step towards a more secure digital landscape. In an era where IoT devices are becoming ubiquitous, manufacturers must prioritize security from the outset. By leveraging Exein's comprehensive IoT security solutions, manufacturers can achieve CRA compliance and strengthen their defenses against the dynamic threat landscape. Therefore, the path to a smarter, safer world is charted by the synergy between innovative cybersecurity measures and regulatory compliance.
The CRA Roadmap: A Timeline for Manufacturers
First proposed in September 2022, the Cyber Resilience Act (CRA) gained initial approval from the Council in December 2023 and was officially endorsed by the European Parliament in March 2024. With final adoption by the Council expected in November 2024, manufacturers will have a 36-month grace period to comply with the new regulations, except for incident and vulnerability reporting which requires a shorter 21-month window. This means manufacturers must have systems in place to report these issues by August 2026, with all other CRA requirements coming into effect by November 2027.




