Exein Runtime Application on Industrial Infrastructure

The manufacturing landscape has undergone a remarkable transformation with the advent of Industry 4.0 and the extensive adoption of the Internet of Things (IoT).
In this era of interconnected devices, it is crucial to comprehend the potential risks associated with compromised connected devices and the significance of defending against such threats.
From cloud infrastructures to Human Machine Interfaces, hackers have discovered numerous ways to breach critical infrastructures.
We've created an infographic that illustrates how our solution helps to encounter cyber threats in an easy-to-digest format.
Take a visual journey with us into Runtime Architecture for Industrial Infrastructures and discover how Exein is pioneering cybersecurity and keeping manufacturers one step ahead of the game.
Infographic breakdown
With the proliferation of IoT devices in the manufacturing industry, a new era of cybersecurity risks has emerged, requiring robust measures to safeguard sensitive data, critical infrastructure, and ensure the continuity of operations.
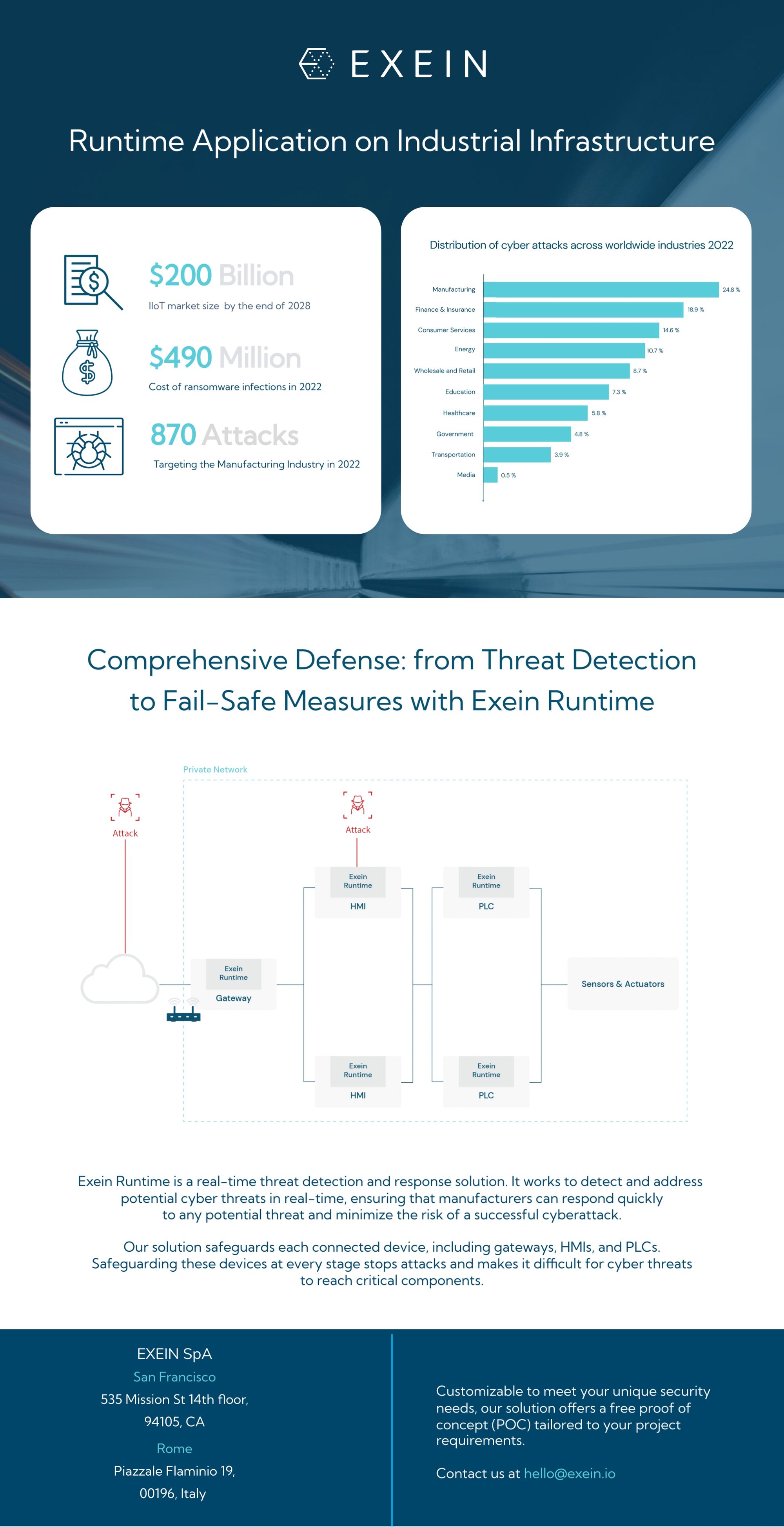
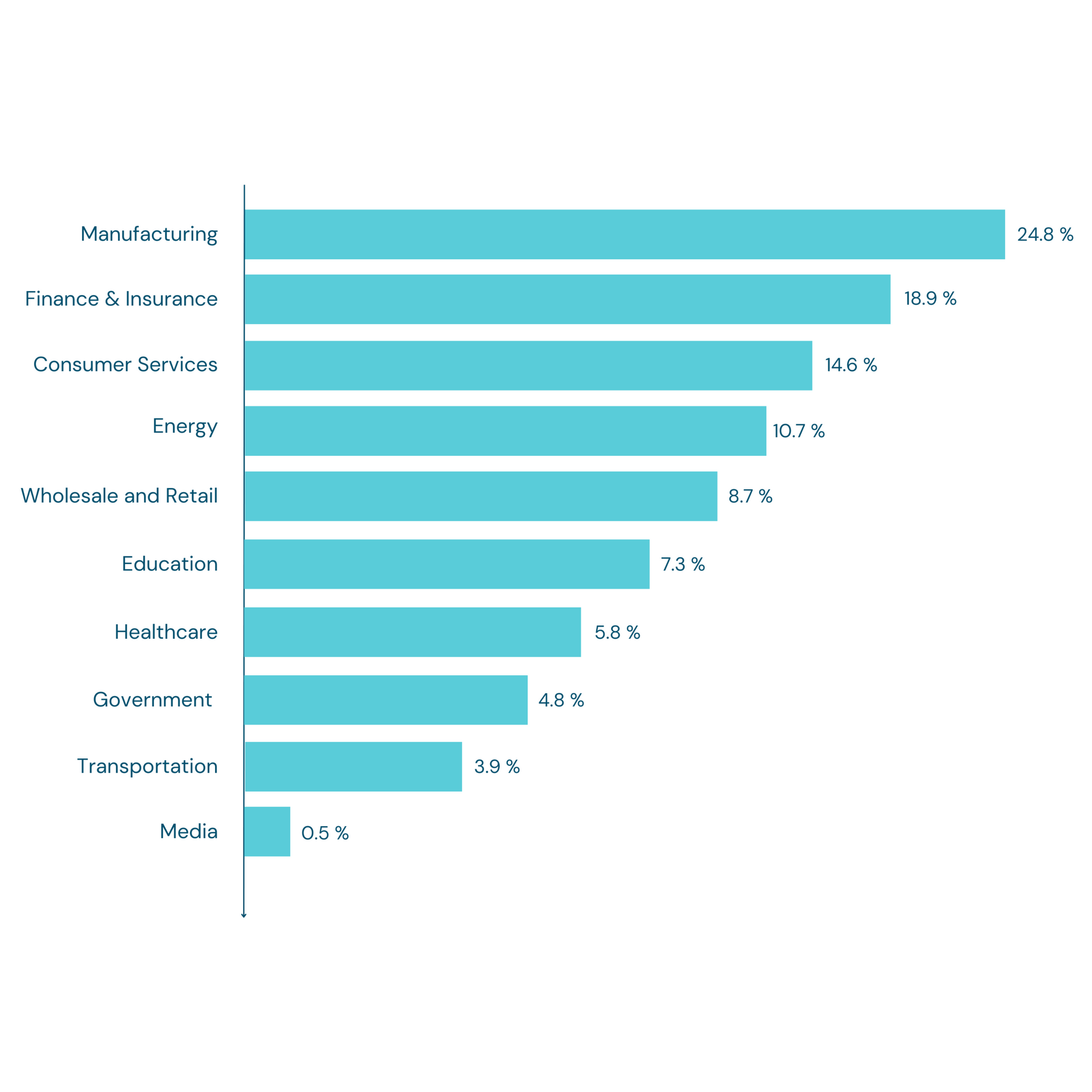
According to statistics, in 2022 manufacturing had the highest share of cyber attacks among the leading industries worldwide. During the examined year, cyber attacks in manufacturing companies accounted for nearly 25% of the total cyber attacks.
In 2022 there have been around 870 attacks targeting the manufacturing industry and the costs of ransomware infections went up to $490 Million.
By 2028, the IIoT market size is projected to generate approximately $200 billion in revenue.

By prioritizing robust cybersecurity throughout the industrial ecosystem, the industry can embrace IIoT benefits while ensuring the utmost safety and security for all stakeholders involved.
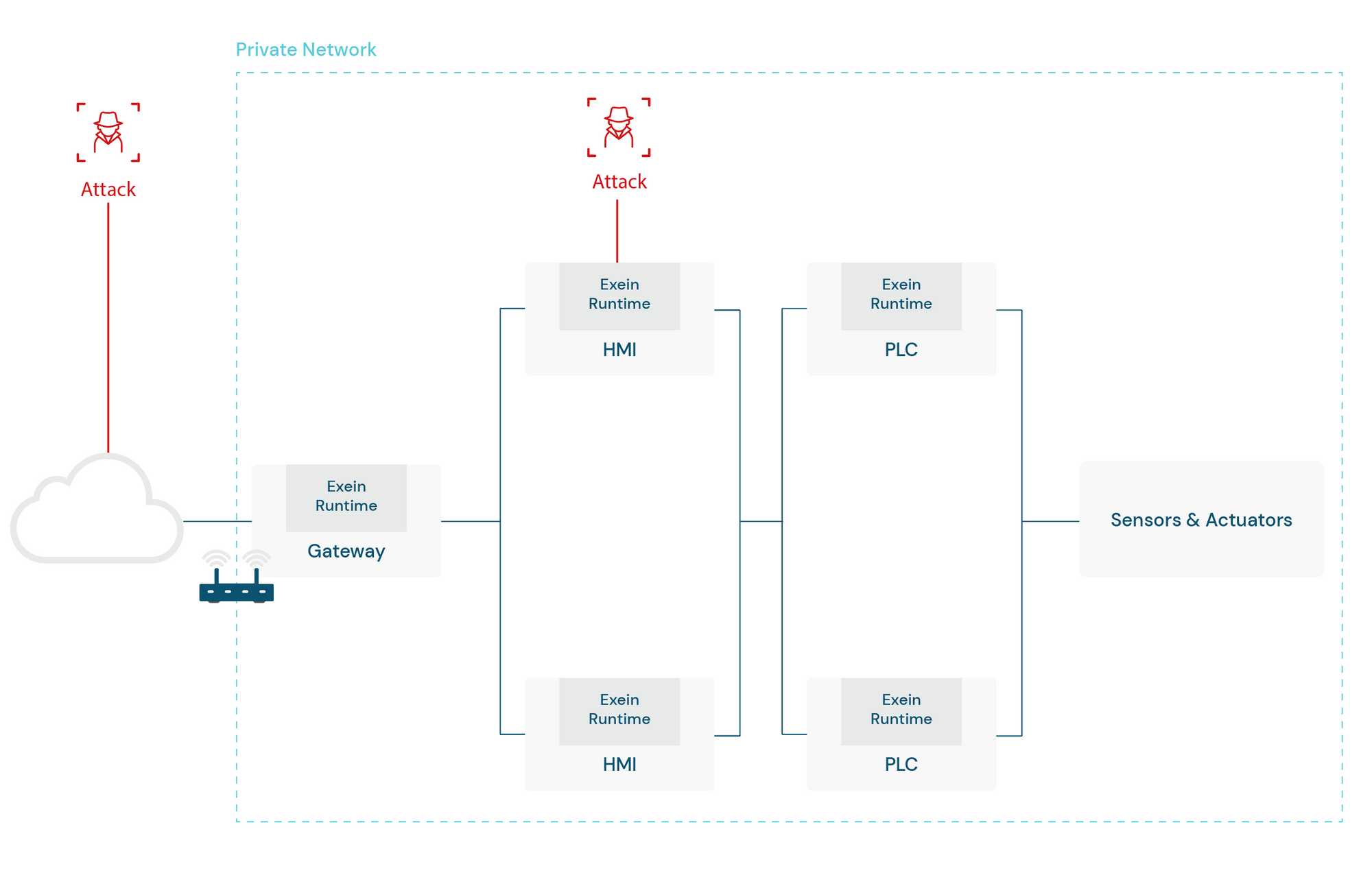
Runtime Architecture
In our infographic, we have identified two potential attack scenarios: the first scenario represents an external attack originating from the cloud infrastructure exposed to the public network. In this case, Exein Runtime, positioned on the Gateway, effectively blocks the attack before it can reach the organization's internal network.
The second scenario portrays an attack generated from within the company's private network, aiming to manipulate the operation of a machinery through vulnerabilities in the Human Machine Interface (HMI). Here, Exein Runtime, deployed on the HMI, detects and blocks any anomalous activity, ensuring the protection of critical system components.
What sets Exein Runtime apart is its ability to autonomously secure each individual device within the organization, ensuring comprehensive protection across multiple levels. This multi-layered approach safeguards critical components responsible for product output, mitigating potential attacks from both external and internal sources.
Our security solution is continuously updated and highly customizable, offering unparalleled protection. Exein Runtime seamlessly integrates with existing embedded devices and can be seamlessly incorporated into your existing software solutions.
Our enterprise-class security solutions provide organizations with the right combination of monitoring, protection and response capabilities to reduce the risk of cyber attacks.
At Exein we recognize that every organization has unique security needs, which is why our solutions are customizable to meet those specific requirements.
If you are unsure about what’s the most appropriate solution for your company, our team of experts will work with you to understand your project requirements and provide a proof of concept (POC) that is entirely free of charge.
During the POC, we will discuss how our technology can help solve your security problems and provide an opportunity to see it in action.
Contact us at hello@exein.io




