Industrial IoT Security for Safer, More Efficient Workplaces: Insights for Chief Security Officers

The Industrial Internet of Things (IIoT) has become an integral part of industrial operations, offering significant enhancements in efficiency and safety. However, ensuring the security of these complex systems presents a considerable challenge. As Chief Security Officers (CSOs), the task falls on you to navigate this challenge, armed with an understanding that the primary goal of IIoT security protocols should not be confined to the avoidance of system failures alone.
Today's digital landscape is vast and intricate. IIoT networks, the algorithms that fuel them, and the colossal data they process have grown so sophisticated and fragile that failures have become a built-in aspect of these systems, rather than an occasional anomaly.
Unlike AI systems, IIoT systems are not inherently probabilistic. Yet, they too are vulnerable to errors, not due to any innate probabilistic nature, but owing to their escalating complexity. As these systems evolve, they unwittingly give birth to an array of potential failure points. Hence, the focus of IIoT security should transition from a narrow objective of preventing breaches to a broader, more pragmatic approach of detecting and responding to vulnerabilities when they inevitably occur.
One promising strategy to navigate these challenges involves adopting zero trust architectures. These frameworks operate under the assumption that all systems, irrespective of their origin, can potentially be compromised by adversaries. This concept is not merely theoretical—it has gained recognition and been deployed by government institutions, with the U.S. government, for instance, integrating a zero trust strategy across various departments and agencies.
However, the adoption of zero trust architectures is just one facet of the larger scheme of adapting to and managing failures in IIoT systems. It's critical for organizations to invest heavily in their incident response programs, introducing robust measures to handle potential breaches and vulnerabilities. Such measures may include conducting 'red team' exercises, which simulate potential attacks and identify weaknesses in the software and IIoT systems, thereby enhancing the effectiveness of incident response planning.
Beyond these technical considerations, we must remember that IIoT's transformative potential lies in its capacity to foster safer and more efficient workplaces. When properly secured, IIoT devices can significantly enhance employee safety by minimizing the risk of accidents and equipment malfunctions. Sensors and automated systems can continuously monitor environmental conditions, detect anomalies, and implement corrective actions more quickly and accurately than humans can.
Furthermore, IIoT can have a profound impact on operational efficiency. Secure IIoT devices can streamline processes, optimize resource utilization, and boost productivity. They enable predictive maintenance, reducing downtime by identifying potential failures before they occur. Additionally, the data harvested from IIoT devices can be analyzed to glean insights and make data-driven decisions, leading to continuous improvement in operational efficiency.
However, all these benefits hinge on effective IIoT security. A compromised IIoT device can lead not only to operational disruptions but also to significant safety hazards. For instance, a manipulated sensor might fail to detect hazardous conditions, endangering workers' lives. Therefore, a proactive and comprehensive approach to IIoT security is a prerequisite to realizing the potential benefits of IIoT in terms of safety and operational efficiency.

In a nutshell, IIoT security must evolve in step with the increasing complexity of these systems and the emerging threat landscape. This necessitates a shift from failure avoidance to failure detection and response, along with the integration of zero trust architectures and the reinforcement of incident response programs. As we traverse this complex landscape, we must keep in mind that our ultimate goal extends beyond mere system protection. We aim to establish safer, more efficient workplaces, thereby transforming the promise of IIoT into reality and unlocking its full potential.
As we move forward, we must also understand the importance of continuous education and training for all staff members. Everyone, from the highest-level executives to the newest employees, should be aware of the potential security risks inherent in IIoT systems. They should be trained to identify and respond to security threats, and understand the importance of adhering to established security protocols. This human-centric approach to IIoT security is essential in building a resilient system that can withstand attacks and recover quickly from any breaches.
Moreover, we must recognize the importance of a proactive approach to security. This includes regular system audits to identify potential vulnerabilities, as well as the development and implementation of incident response plans to ensure rapid and effective action in the event of a breach.
On top of that, organizations should also embrace a philosophy of continuous improvement when it comes to IIoT security. This involves regularly reviewing and updating security protocols in response to new threats and technological advancements. It also means investing in new technologies and tools to enhance system security and resilience.
The integration of advanced technologies such as machine learning and artificial intelligence can also play a pivotal role in enhancing IIoT security. These technologies can help automate and improve the process of threat detection and response, making the system more efficient and effective.
It's crucial to remember that while technology plays a significant role in IIoT security, it is not the only factor. A strong organizational culture that values security is equally important. This includes promoting a culture of accountability and responsibility, where every member of the organization understands their role in maintaining system security.
In conclusion, effective IIoT security is not just about technology and protocols. It is also about people and culture. It's about ensuring that every member of the organization understands the importance of security and is committed to maintaining it. It's about creating a culture of continuous learning and improvement, where new threats are identified and addressed promptly, and lessons learned from past incidents are used to strengthen the system.
By taking such a comprehensive and proactive approach to IIoT security, we can not only protect our systems and data but also ensure the safety of our employees and the efficiency of our operations. In doing so, we can truly realize the promise of the Industrial Internet of Things, creating safer, more efficient workplaces for all.
The Embedded Security
Another crucial element in fortifying IIoT security lies in the effective deployment of dedicated cybersecurity solutions. An exemplary tool in this context is Exein Runtime, a new generation of embedded security system specifically designed for IIoT devices. This product can provide CSOs with an advanced protective layer for their IIoT environments, making the job of securing these complex networks much more manageable.
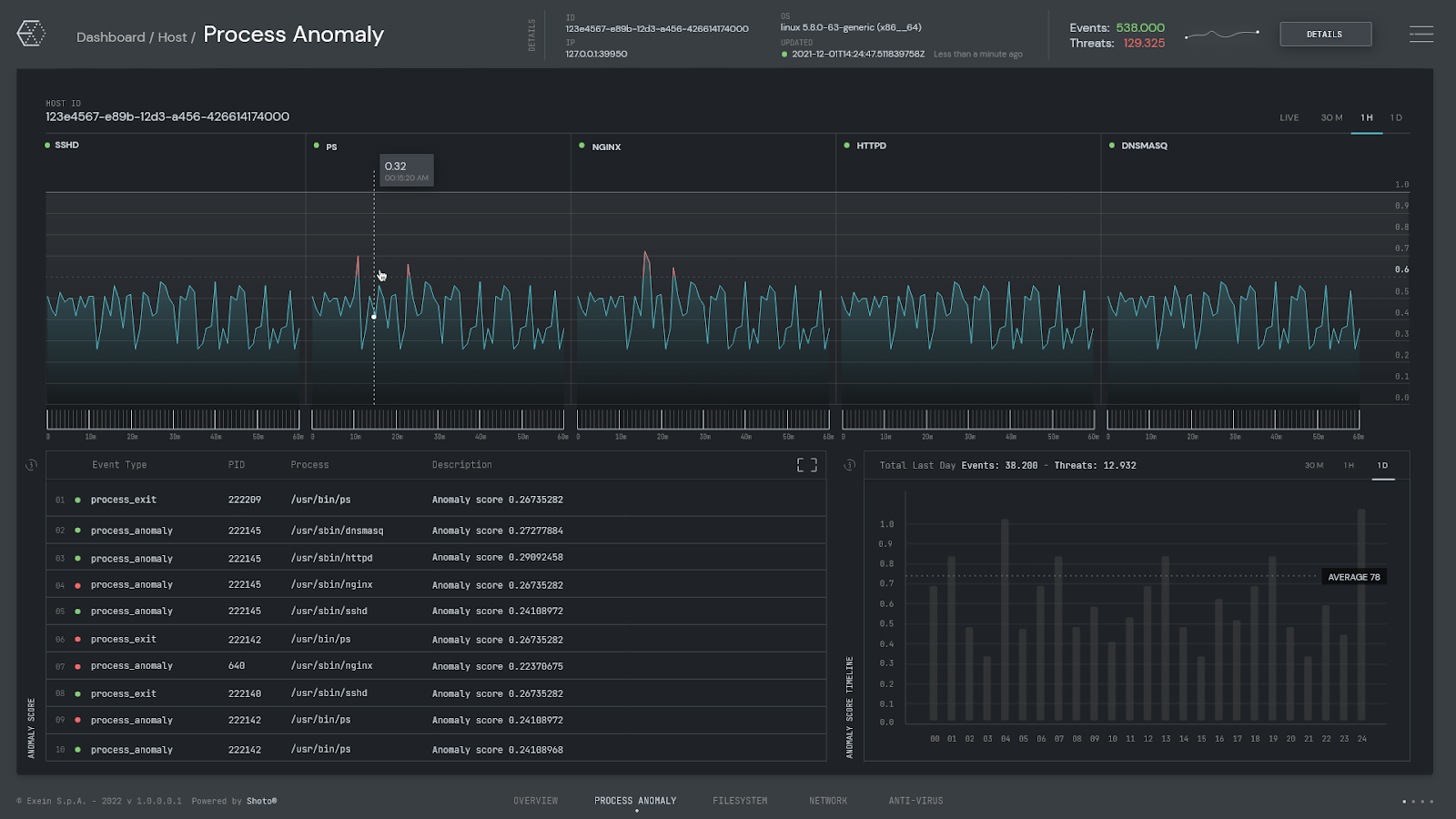
Exein Runtime works by being directly integrated into the firmware of IIoT devices, providing a deep layer of defense that's resistant to many common attack vectors. By operating at the firmware level, it can monitor and control the behavior of the device, effectively preventing anomalous activities and potential intrusions. This approach allows Exein Runtime to detect and block threats that conventional network-based security systems might overlook.
In addition to its powerful intrusion detection and prevention capabilities, Exein Runtime also provides a suite of features that can aid CSOs in effectively managing their IIoT security. These include real-time monitoring and alerts, detailed threat analytics, and automated response capabilities, among others.
Exein Runtime uses machine learning algorithms to establish the normal behavior of the IIoT devices it protects. It continuously monitors the devices for deviations from this norm, allowing it to detect potential threats as soon as they emerge. This proactive approach to security ensures that threats are detected and neutralized in their early stages, minimizing the potential damage they can cause.
Moreover, by providing a comprehensive, all-in-one security solution, Exein Runtime can simplify the task of managing IIoT security, freeing up resources for other critical tasks. For CSOs, this means less time and effort spent on day-to-day security management and more focus on strategic planning and risk mitigation.
Exein Runtime represents a significant advancement for IIoT security. Its deep, firmware-level protection, combined with its advanced threat detection and management features, make it an invaluable tool for CSOs looking to secure their IIoT environments. By leveraging solutions like Exein Runtime, organizations can better protect their IIoT devices, ensuring not only the integrity of their operations but also the safety of their employees.
Want to know more? Download our exclusive one-pager and elevate your IIoT security with Exein.





