Runtime Application on Healthcare Appliances

IoMT, short for the Internet of Medical Things, encompasses a network of interconnected medical devices and applications that communicate with healthcare information technology systems via the internet. These devices, spanning medical equipment, wearables, sensors, and more, are crafted to collect and exchange healthcare data, facilitating monitoring, diagnosis, and treatment. Despite their transformative potential, the widespread integration of IoMT technologies has introduced significant security challenges, rendering the healthcare sector highly susceptible to cyber threats.
We've created an infographic that illustrates how our solution helps to encounter cyber threats in an easy-to-digest format.
Take a visual journey with us into Runtime Architecture for Healthcare Appliances and discover how Exein is pioneering cybersecurity and keeping IoMT manufacturers one step ahead of the game.
Infographic breakdown
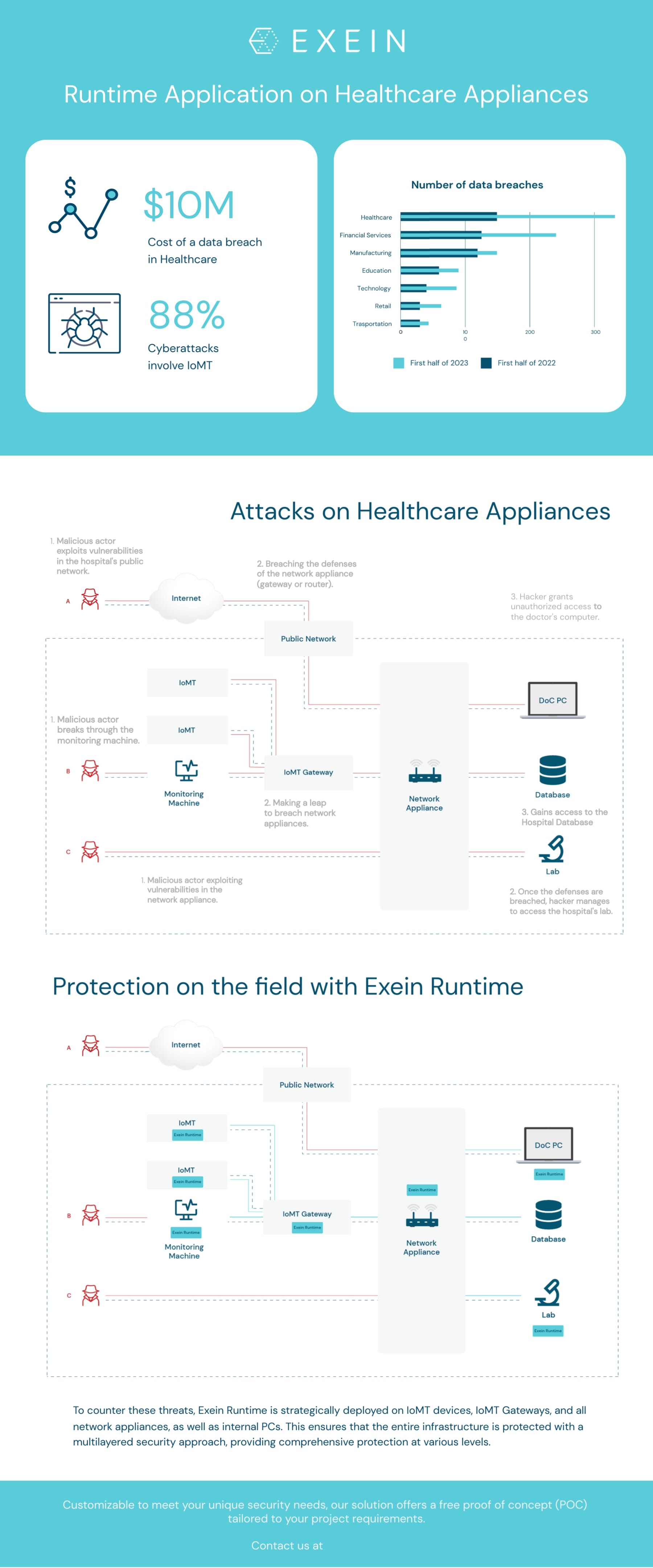
According to statistics the average cost of a data breach is $4 million, but in healthcare, it soars to an average of $10 million.
88% of cyberattacks on healthcare systems involve IoMT and 12% are rooted in IoT.
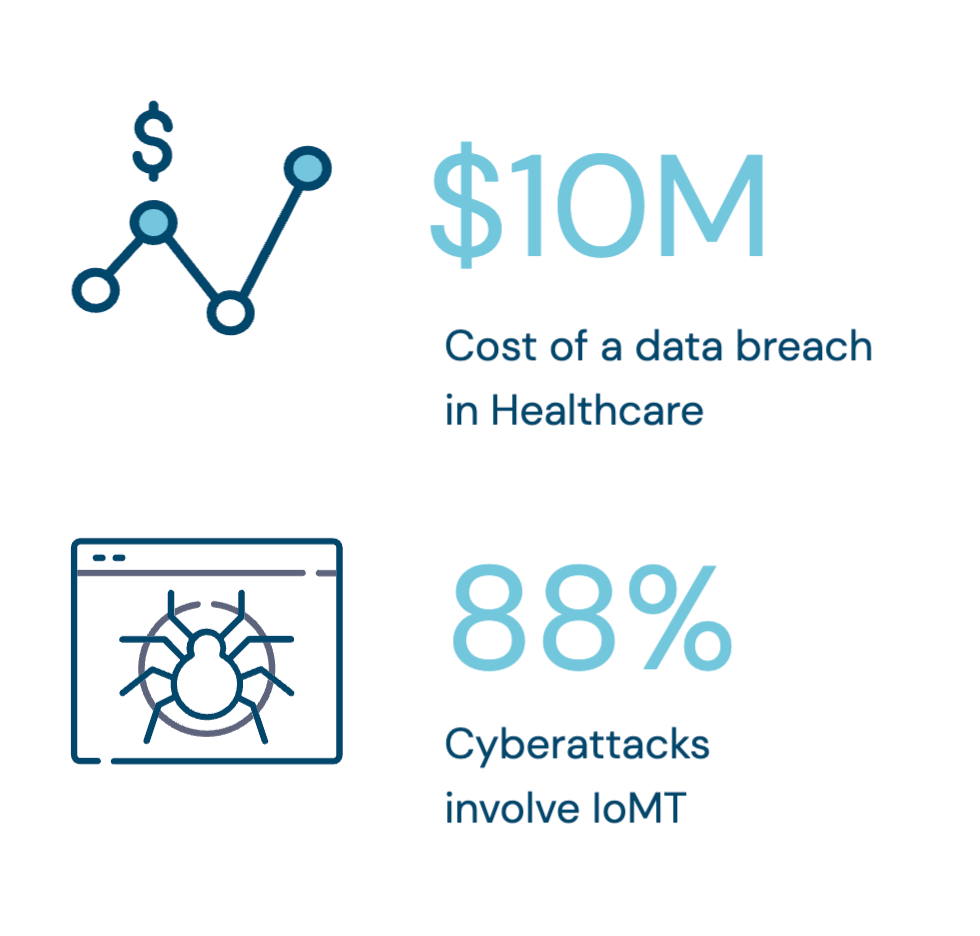
Healthcare organizations had 379 compromises in the first half of 2023, compared to 161 in the prior year's first half.
By prioritizing robust cybersecurity throughout the devices lifecycle, the industry can embrace IoMT benefits while ensuring the utmost safety and security for both manufacturers and patients.
Runtime Architecture
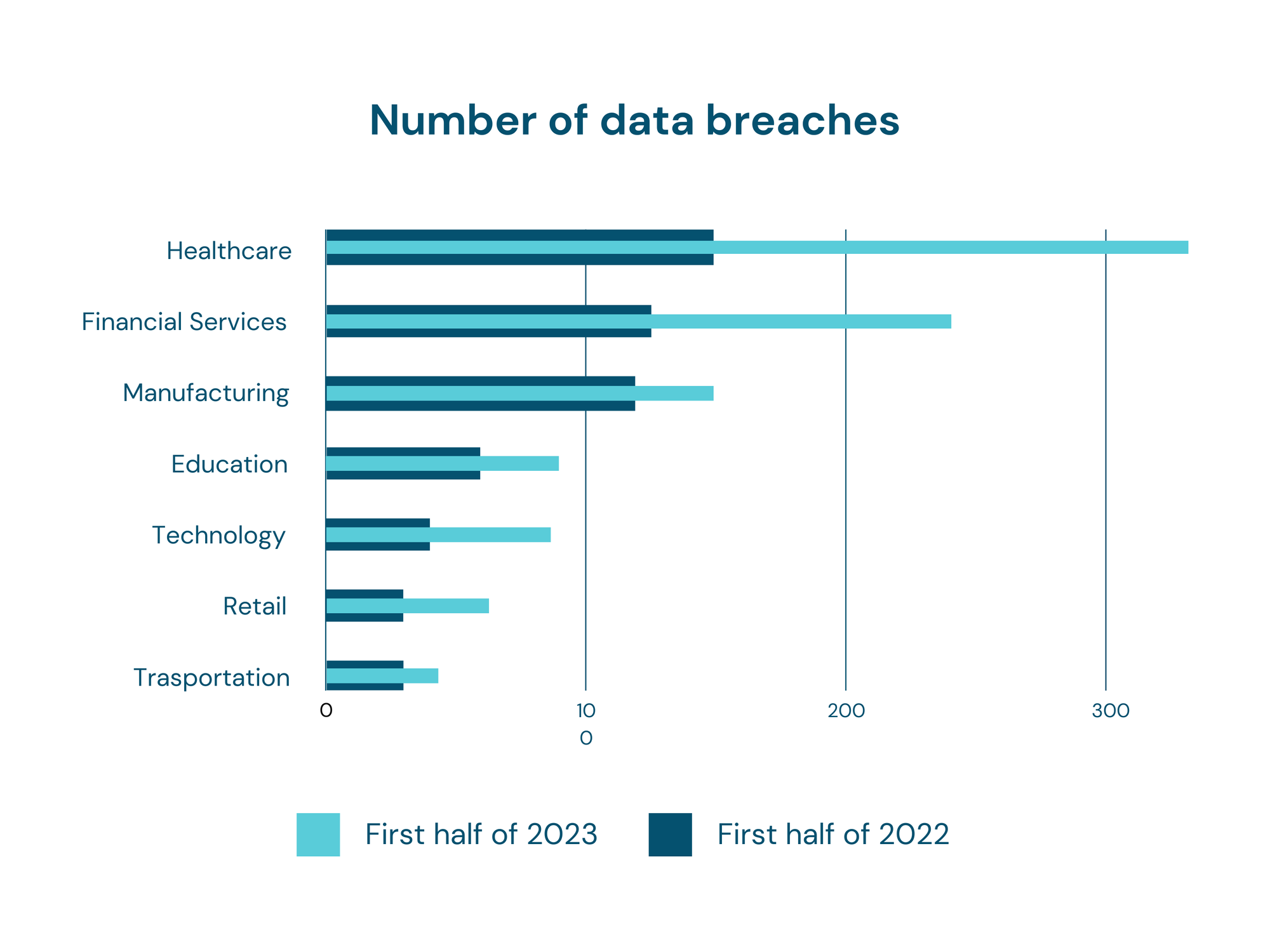
In a hospital's intricate digital ecosystem, various components seamlessly interconnect to optimize patient care while presenting a complex network susceptible to cyber threats.
We have identified three potential attacks targeting a hospital, each with the objective of illicitly obtaining specific information, such as patient or financial data.
The first attack (A) occurs remotely over the internet, as a malicious actor exploits vulnerabilities in the hospital's public network, successfully breaching the defenses of the network appliance(gateway or router). This unauthorized intrusion could potentially provide access to the doctor's computer, allowing the attacker to manipulate connected devices and/or gain entry to sensitive hospital information.
Attack B is carried out locally, effectively infiltrating the monitoring machine before advancing to compromise network appliances. Subsequently, it gains entry to the Database, which may house both patient data and the financial information of the hospital.
Attack C, also occurring locally, exploits vulnerabilities in the network appliance. Upon successfully breaching the defenses, it gains access to the laboratory.
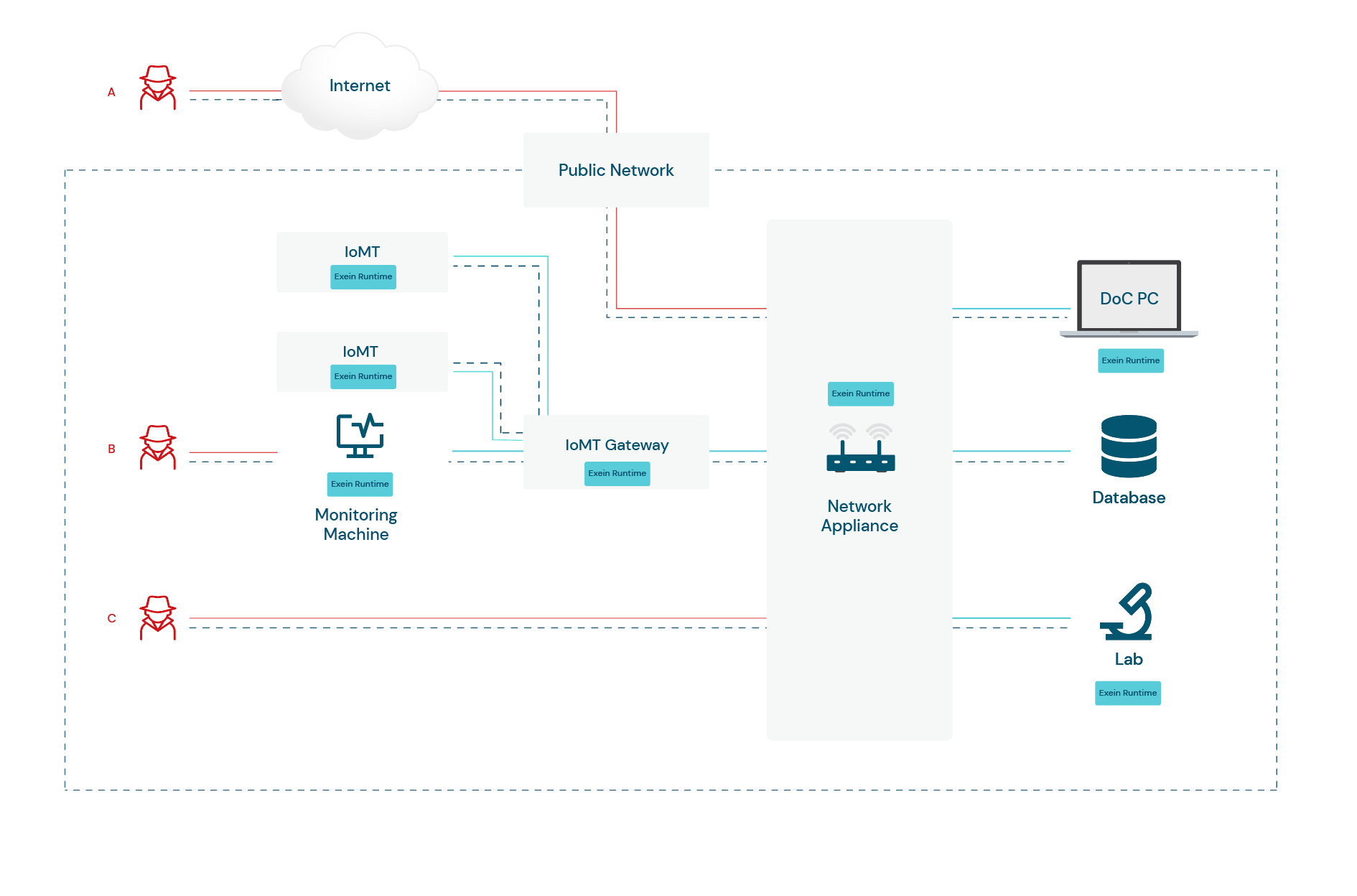
In all the attack scenarios we've illustrated before, the potential consequences include compromised patient privacy and security, disruption of medical services, potential financial losses, and damage to the hospital's reputation.
To counter these threats, Exein Runtime is strategically deployed on IoMT devices, IoMT Gateways, and all network appliances, as well as internal PCs.
This ensures that the entire infrastructure is protected with a multilayered security approach, providing comprehensive protection at various levels.
Our end-to-end security solution continuously evolves and is highly customizable to adapt to emerging threats, it's proactive approach stops potential attacks in their tracks, safeguarding both the connected devices and the integrity of the data they transmit.
Our enterprise-class security solutions provide organizations with the right combination of monitoring, protection and response capabilities to reduce the risk of cyber attacks.
At Exein we recognize that every organization has unique security needs, which is why our solutions are customizable to meet those specific requirements.
If you are unsure about what’s the most appropriate solution for your company, our team of experts will work with you to understand your project requirements and provide a proof of concept (POC) that is entirely free of charge.
During the POC, we will discuss how our technology can help solve your security problems and provide an opportunity to see it in action.
Contact us at hello@exein.io




