Exein Runtime Application on Smart Home Appliances

Smart homes have evolved rapidly, bringing unprecedented convenience and automation to our lives.
As IoT becomes deeply integrated into our daily routines, ensuring the safety and reliability of smart home devices is now a top priority.
Manufacturers of IoT devices for smart homes are at the forefront of shaping this evolving industry.
While prioritizing user-friendly features and seamless functionality, manufacturers have to ensure that their products offer robust security, safeguarding both user privacy and their own reputation.
Hackers have discovered numerous ways to breach smart homes, ranging from exploiting vulnerabilities in gateways and central routers to targeting IoT devices themselves.
We've created an infographic that illustrates how our solution helps to encounter cyber threats in an easy-to-digest format.
Take a visual journey with us into Runtime Architecture for Smart Home Appliances and discover how Exein is pioneering cybersecurity and keeping manufacturers one step ahead of the game.
Infographic breakdown
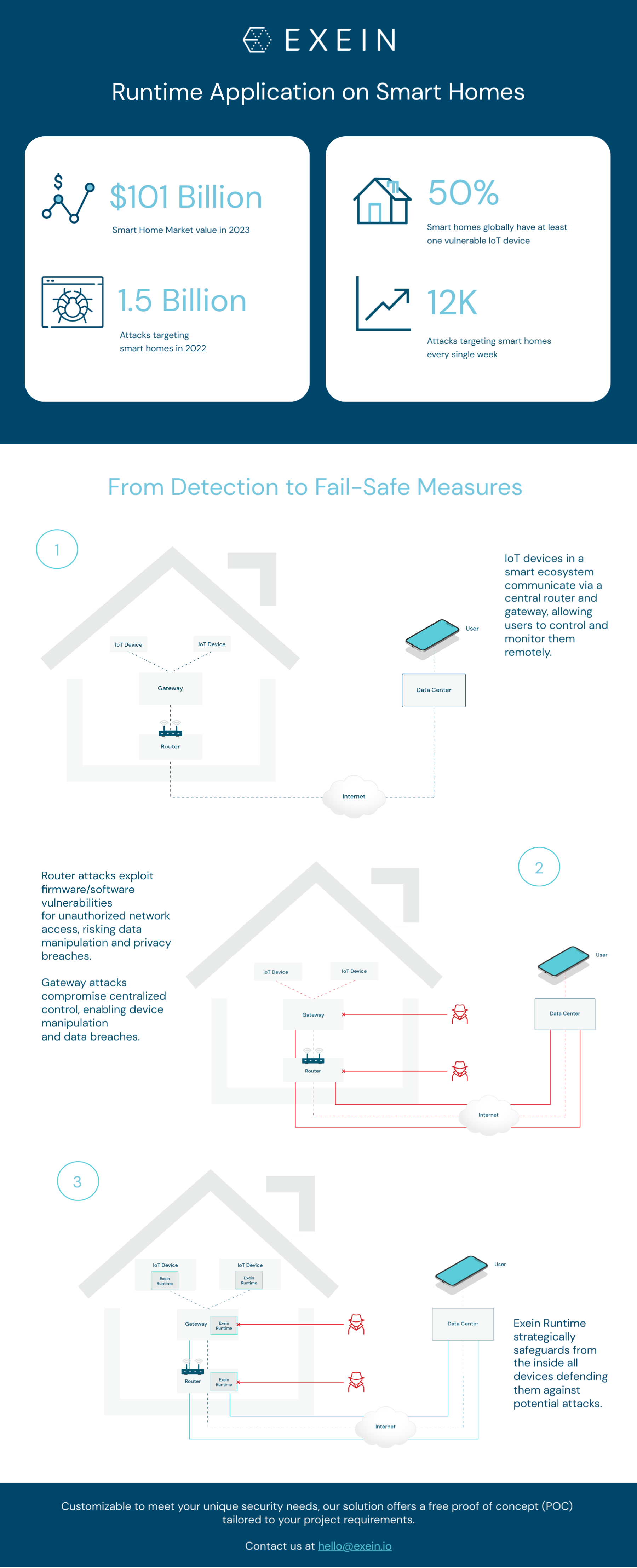
According to statistics there have been 1.5 Billion attacks targeting smart homes in 2022.
Today, in 2023, there are around 12k attacks targeting smart homes every week and this happens mainly because 50% of smart homes globally have at least 1 vulnerable IoT device in their homes.

By prioritizing robust cybersecurity throughout the devices lifecycle, the industry can embrace IoT benefits while ensuring the utmost safety and security for both manufacturers and end users.
Runtime Architecture
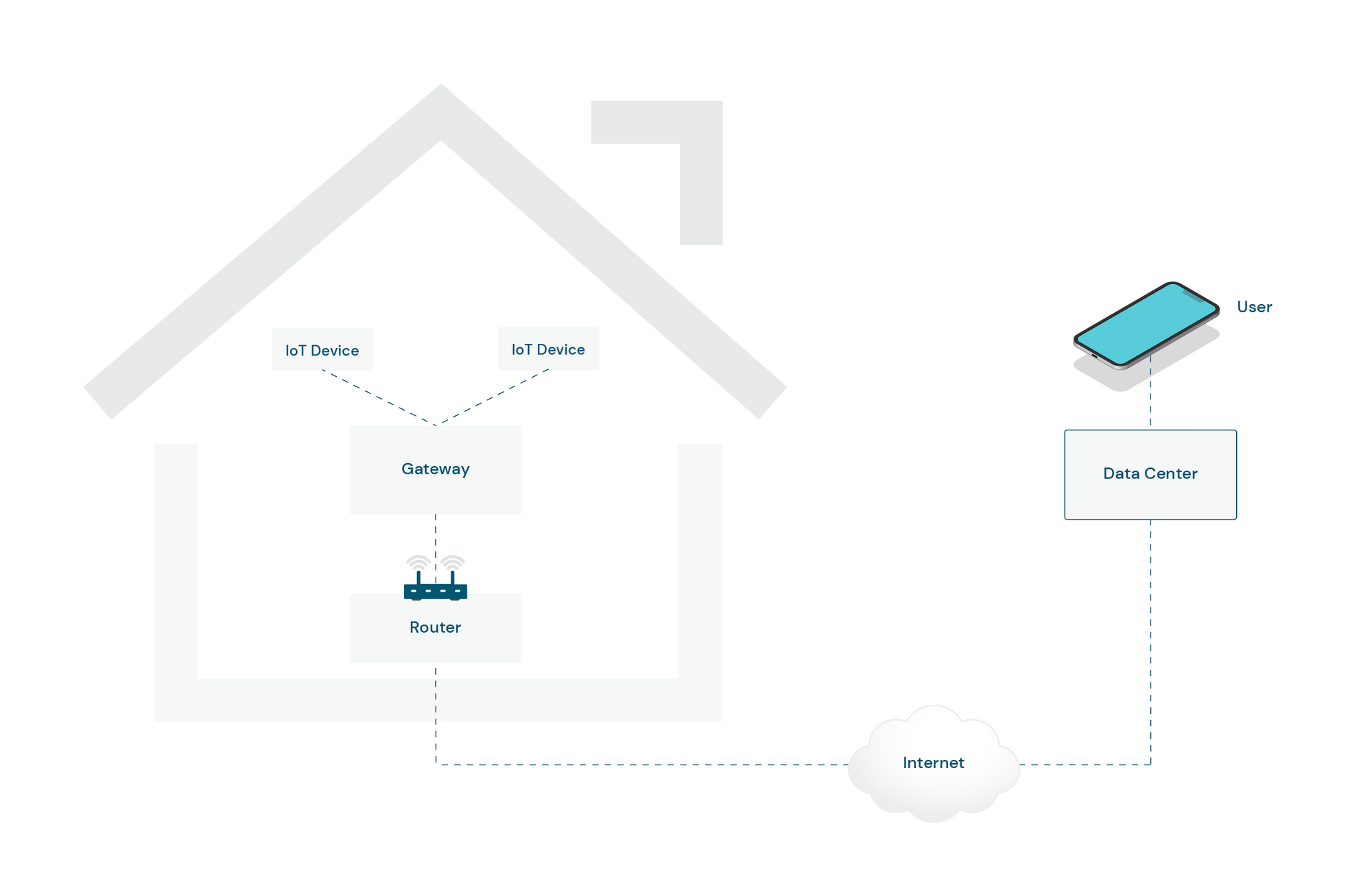
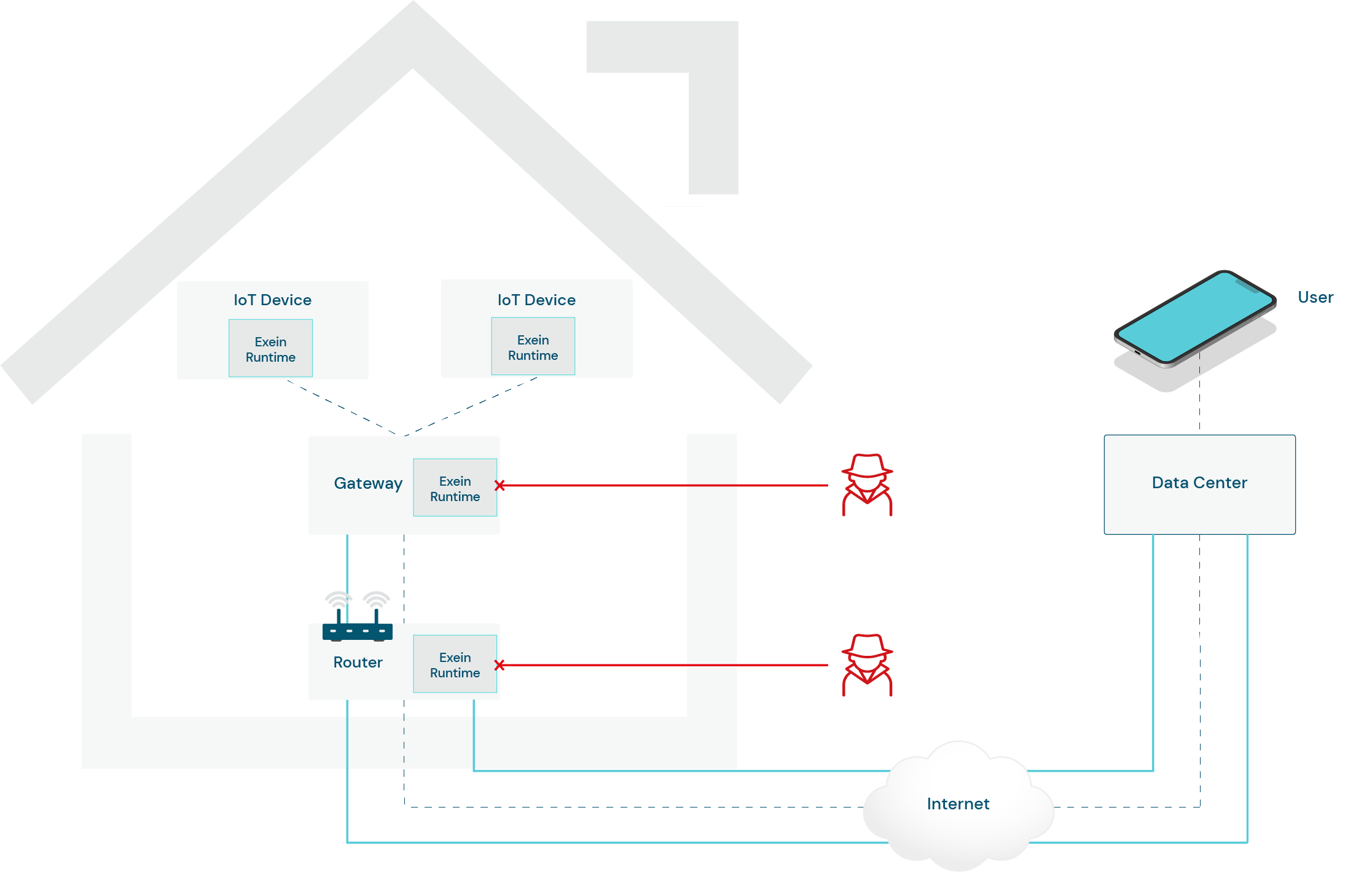
In examining the architecture of a conventional connected home, a prevalent scenario emerges where homeowners can seamlessly interact with their smart devices, even when they are away from their residence.
This interconnected ecosystem relies on the synergy between various IoT devices, which communicate among themselves and establish connections with a central router and gateway.
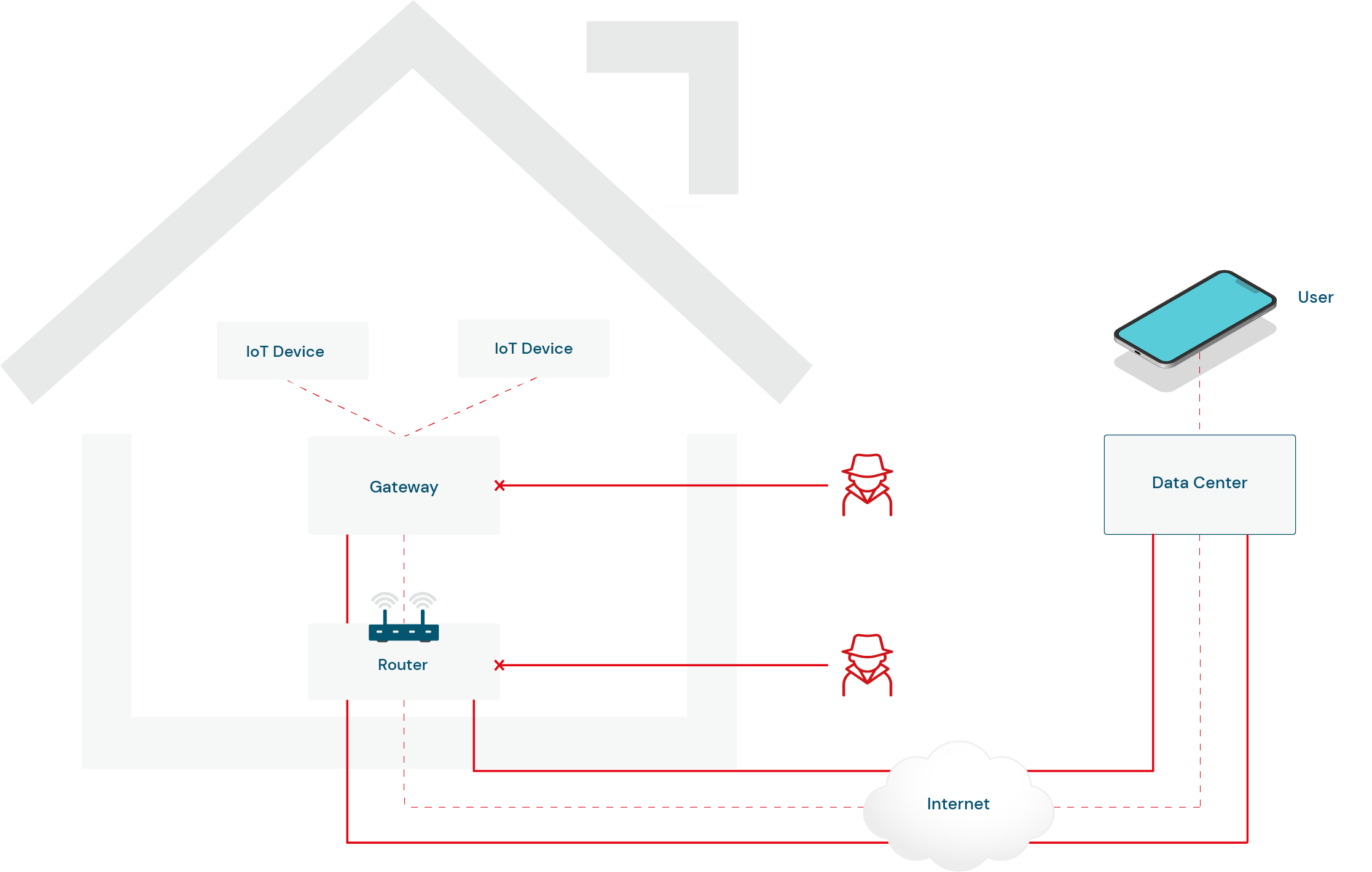
We identified two potential attack scenarios within the context of a smart home architecture.
First, an attack directed at the router involves exploiting vulnerabilities in its firmware or software, granting the attacker unauthorized access to the home network.
Once inside, the attacker intercepts and manipulates data traffic between IoT devices and the data center, potentially compromising user privacy and gaining control over the connected devices.
Similarly, targeting the gateway offers another avenue for intrusion. An attacker exploiting vulnerabilities in the gateway's security could potentially compromise the centralized control point of the smart home ecosystem.
This breach would enables the attacker to manipulate the communication between IoT devices and the gateway, taking control of these devices and compromising the integrity of the data transmitted.
To counter these threats, Exein Runtime is strategically deployed on the Router, Gateway and IoT devices ensuring comprehensive protection at multiple levels.
This strategic placement acts as a robust defense mechanism against potential attacks, preventing unauthorized access and manipulation of data within the smart home ecosystem.
Our end-to-end security solution continuously evolves and is highly customizable to adapt to emerging threats, it's proactive approach stops potential attacks in their tracks, safeguarding both the connected devices and the integrity of the data they transmit.
Our enterprise-class security solutions provide organizations with the right combination of monitoring, protection and response capabilities to reduce the risk of cyber attacks.
At Exein we recognize that every organization has unique security needs, which is why our solutions are customizable to meet those specific requirements.
If you are unsure about what’s the most appropriate solution for your company, our team of experts will work with you to understand your project requirements and provide a proof of concept (POC) that is entirely free of charge.
During the POC, we will discuss how our technology can help solve your security problems and provide an opportunity to see it in action.